"Our integration with the Google Nest smart thermostats through Aidoo Pro represents an unprecedented leap forward for our industry."
- Antonio Mediato, founder and CEO of Airzone.
Over the last decade, I have worked closely with CIOs, CTOs, and Heads of Engineering across manufacturing, healthcare, logistics, and finance. One pattern keeps repeating. Enterprises no longer ask if they need a mobile app. They ask how secure it will be once it is live.
Mobile apps now sit at the center of enterprise workflows. They handle customer data, employee access, financial records, location details, and operational systems. One weak link can expose years of trust and millions in revenue.
This is where a Custom Mobile App Development Company plays a critical role. Security is not something added at the end. It is built into every decision from architecture to deployment and long after launch.
In this blog, I will walk you through how experienced teams actually build secure enterprise mobile apps. I will also break down what most top ranking blogs miss and share real insights I have gathered from C level leaders who have lived through security failures and successes.
One of the biggest mistakes enterprises make is treating security as a development phase. In reality, security begins much earlier.
When we work with enterprise clients at Softura, the first conversations are not about features. They are about risk.
Questions we ask upfront
A seasoned Custom Mobile App Development Company treats these questions as foundational. Without them, even the most advanced security tools will fail.
I once worked with a global logistics firm whose app was technically secure but failed due to unclear access policies. Field workers shared credentials. No amount of encryption could fix that.
Security must align with how people actually work.
"Our integration with the Google Nest smart thermostats through Aidoo Pro represents an unprecedented leap forward for our industry."
- Antonio Mediato, founder and CEO of Airzone.
If I had to point to one area that separates average vendors from enterprise grade partners, it would be architecture.
Secure architecture answers questions like
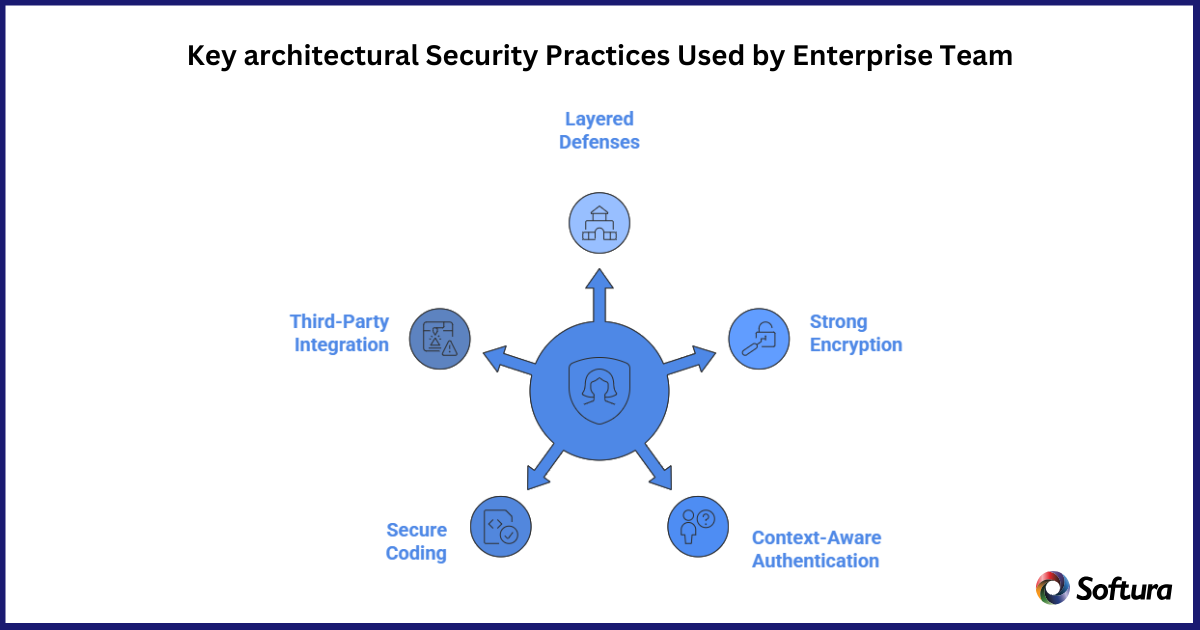
A reliable Custom Mobile App Development Company designs apps with layered security. This means even if one layer is compromised, others remain intact.
Key architectural principles include
Strong separation between mobile app, backend services, and databases
One CTO from a healthcare enterprise told me something I still quote
We stopped thinking of our mobile app as a product and started treating it like infrastructure. Security became non negotiable.
That mindset shift changes everything.
"By analyzing the data from our connected lights, devices and systems, our goal is to create additional value for our customers through data-enabled services that unlock new capabilities and experiences."
- Harsh Chitale, leader of Philips Lighting’s Professional Business.
Enterprise mobile apps handle sensitive data. Customer identities. Payment records. Internal reports. Losing control of this data is often more damaging than downtime.
A Custom Mobile App Development Company approaches data security on three levels
Data at rest is protected using strong encryption and secure storage mechanisms on the device and server.
Data in transit is secured using trusted communication protocols and certificate validation.
Data in use is where many apps fail. Screenshots, background processes, and caching can expose data unintentionally.
I have seen enterprises fix server security only to leak data through simple UI behaviors. This is why mobile security requires specialized experience.
Passwords alone are no longer enough. Enterprises know this. Attackers know it too.
A mature Custom Mobile App Development Company designs authentication systems that match enterprise risk levels.
Common practices include
But the real value comes from context aware access. For example
An employee accessing sensitive data from an unknown location triggers additional verification
An inactive session automatically expires
A CIO from a financial services firm once told me
We did not get breached because our tech failed. We got breached because access rules were too loose.
Security is often about discipline more than tools.
Many blogs list secure coding as a checklist item. In reality, it is a culture.
Experienced teams follow secure coding standards not because a document says so, but because they have seen what happens when shortcuts are taken.
I have personally reviewed apps where a single overlooked input field exposed an entire backend system.
A dependable Custom Mobile App Development Company builds review processes that catch these issues early. Fixing them later is costly and risky.
Enterprise apps rarely operate alone. They connect to payment gateways, analytics tools, ERP systems, and cloud services.
Each integration increases risk.
Top development partners evaluate third party tools as carefully as they write their own code.
Key checks include
One retail enterprise learned this the hard way when a third party analytics SDK exposed customer data. The app itself was secure. The integration was not.
A Custom Mobile App Development Company must own this responsibility, not push it back to the client.
• Secure architecture with layered defenses
• Strong encryption for data at rest and in transit
• Context aware authentication and access control
• Secure coding standards and peer reviews
• Careful evaluation of third party integrations
Security testing is not about checking boxes. It is about thinking like someone who wants to break your system.
Enterprise focused teams perform
I once sat in a security review where a simulated attack exposed a flaw no automated tool detected. Human insight still matters.
A serious Custom Mobile App Development Company invests in security testing because the cost of failure is far higher.
Compliance is often seen as a burden. HIPAA. GDPR. SOC 2. But enterprises cannot ignore it.
The challenge is building compliant apps that users actually want to use.
The best teams integrate compliance into design rather than forcing it later.
For example
Security should protect users, not frustrate them.
Even the most secure app runs on a device you do not control.
A Custom Mobile App Development Company plans for these realities.
Techniques include
Ignoring device risk is like locking your office door but leaving the windows open.
• Clear ownership of security responsibilities
• Defined access and role policies
• Regular security audits
• Incident response planning
• Ongoing security training
Launching an app is not the finish line. It is the starting point.
Threats evolve. Operating systems update. New vulnerabilities emerge.
A long term Custom Mobile App Development Company stays involved.
This includes
One enterprise I advised avoided a major incident because their development partner flagged a new vulnerability early.
Security is a relationship, not a deliverable.
C level executives rarely talk about encryption algorithms. They talk about risk exposure.
From my conversations, their priorities are clear
A Custom Mobile App Development Company that understands this speaks their language.
Security is not sold as fear. It is positioned as stability and resilience.
Off the shelf platforms promise speed. They rarely promise deep security alignment.
Custom development allows enterprises to
This is why many regulated industries choose a Custom Mobile App Development Company over generic tools.
Security is never one size fits all.
After years of building and reviewing enterprise mobile apps, one truth stands out. Secure apps are not accidents.
They are the result of deliberate decisions made by experienced teams who understand technology, business, and human behaviour.
A trusted Custom Mobile App Development Company does not just write code. It builds confidence. It protects reputations. It enables growth without fear.
If you are planning an enterprise mobile app, ask not just how fast it can be built, but how safely it can scale.
If you want to build an enterprise mobile app that balances usability, performance, and real world security, talk to the experts at Softura and start the conversation today.